2. Computer Network Operations¶
Secure Protocols and Virtual Private Networks: An evaluation 1¶
- Network protocols are by their design insecure and open to threats from cyber criminals.
- Secure network protocols, such as L2TP, IPsec, TLS, and OpenVPN need to be implemented to assure confidentiality, authentication, and integrity.
- In general the lower in the stack that a security protocol works, the better. This is because it is preferable for protocols to prevent access to computers on a network (Layer 3), for example, rather than at layers that deal with applications and data (Layers 4-7).
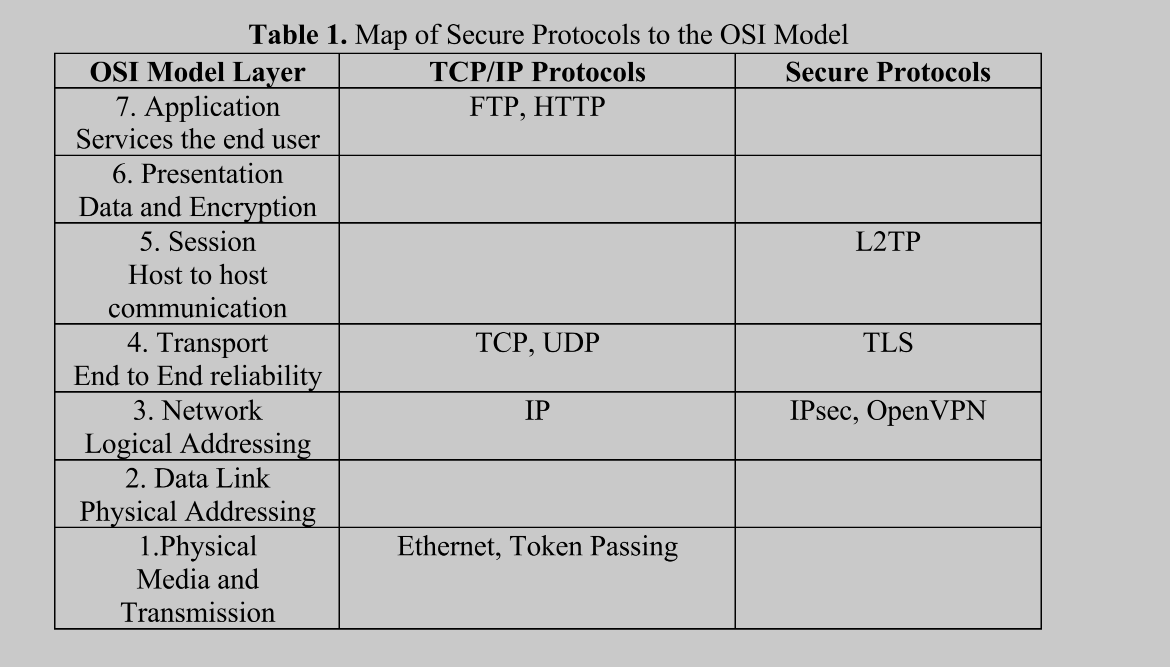
Virtual Private Network (VPN)¶
- Started in 2000s.
- A VPN is a private network within a public network.
- It is a virtual network that spans many physical networks and appears to users as a single network.
- Applications and protocols within a VPN can benefit from security management as if they were connected to a private physical network.
- VPNs use virtual circuits to connect machines on the network, where network configurations and routing tables are dynamic and stored in software; thus ensuring uninterrupted communication.
- A VPN is a virtual encrypted tunnel between the user and a remote server operated by a VPN service.
- All external internet traffic is routed through this tunnel, making information safe from cyber criminals.
- Types of VPN:
- Site-to-Site VPN: Connects two or more networks together.
- Remote Access VPN: Connects individual users to a network from a remote location.
Before VPN¶
- Private networks were used; a company has to manage its private network and own/maintain infrastructure and lines connecting machines on the network.
- Companies had to use leased lines to connect their offices in different locations.
- It was hard for small businesses as upfront costs were high, and running costs were also high.
- Permanent physical circuits were used to connect machines on the network, where network configurations and routing tables were static and stored in hardware.
- To change routing, a network engineer had to physically move cables and reconfigure hardware.
- If something went wrong, communications were lost until the hardware was physically reconfigured or fixed.
What made VPNs possible¶
- The implementation of virtual circuits, or logical, re-routable paths between source ports to the destination ports.
- virtual circuits allowed for dynamic, real-time network maps, and significantly reduced costs when compared to permanent physical circuits and paths of leased lines.
Secure VPN Protocols¶
- These protocols include:
- L2TP: Layer 2 Tunneling Protocol: provides a tunnel to send data, but no real security.
- IPsec: Internet Protocol Security: encrypts IP data (packets) such as the destination and source IP addresses.
- TLS: Transport Layer Security.
- OpenVPN: Open Source VPN.
L2TP¶
- Developed by Microsoft and Cisco.
- Provides logical and physical tunneling: virtual paths between source and destination ports through network nodes (devices, routers, switches, etc).
- L2TP is used by ISPs (Internet Service Providers) to enable VPN services. and then ISP provides them to customers.
- L2TP is similar to the Data Link Layer Protocol in the OSI reference model, in that it connects physical devices as if they are in the same local area network.
- L2TP uses authentication (login), it actually more resembles a session layer protocol.
- L2TP uses UDP (User Datagram Protocol) for data transport, rather than TCP, which makes it faster and more efficient.
- L2TP is not secure by itself, but it becomes encrypted as a service of the IPsec protocol.
- L2TP does not provide encryption or protection to the traffic that passes through the tunnel.
- L2TP is the first step in a secure mode of transportation that involves:
- Encapsulation of IP datagram into the tunneling protocol, thus hiding the original IP datagram while it is in transit.
- This establishes a point-to-point or multi-point link between the communicating parties through a public or shared network.
- It uses DES (Data Encryption Standard) and AES (Advanced Encryption Standard) to encrypt the data: 128 or 256-bit encryption.
- Stats:
- 63% of companies use site-to-site VPNs.
- 90% of working-from-home employees use remote access VPNs.
- Advantages of L2TP:
- Support for both IP and non-IP protocols and networks.
- Support for multiple tunnels.
- Compatibility with NAT (Network Address Translation), which remaps public IP addresses to private ones, thus building firewall protections and keeping the connection while the private IP address changes.
- Support for traffic elimination and flow control that address congestion and keep overhead at a minimum.
- Disadvantages of L2TP:
- L2TP is not secure by itself, it needs to be used with IPsec.
- L2TP is not as fast as PPTP (Point-to-Point Tunneling Protocol).
- L2TP is not as secure as OpenVPN.
- L2TP adds some overhead to IP packets which affects the bandwidth utilization.
IPsec¶
- Often paired with L2TP, the Network Layer protocol IPsec offers data integrity, data confidentiality, and authentication of data.
- IPsec was developed by the Internet Engineering Task Force (IETF).
- It provides a bundle of protocols:
- ISAKMP (IPsec Key Exchange and Management Protocol): for key management, which specifies the negotiation and establishment of security.
- IKE (Internet Key Exchange): for key exchange, which creates a secure channel to protect the negotiation in the set up of the IPsec tunnel for traffic protection.
- AH (Authentication Header): for authentication originality and integrity.
- ESP (Encapsulated Security Payload) offers authentication originality, connectionless integrity, anti-replay service, and data confidentiality, to assure cryptography-based security to the information that is transmitted over the network
- Advantages of IPsec:
- Strong Security with complex encryption and hashing algorithms.
- Provides confidentiality by encrypting data payload.
- Provides integrity by computing checksums or hashes at every communication endpoint.
- Provides authentication using signatures and certificates.
- Protects against spoofing and session hijacking.
- Disadvantages of IPsec:
- IPsec is complex and difficult to configure.
- IPsec is vulnerable to login cracking: The attack involves recovering the Internet Protocol Security (IPsec) Pre-shared secret key (PSK) by using brute force attacks on VPN authentication protocols, but it is a discoverable and easy-to-manage attack.
TLS¶
- TLS is an improved version of SSL (Secure Sockets Layer).
- HTTPS is encrypted using TLS/SSL.
- TLS works in between Layer 4 (Transport Layer) and Layer 7 (Application Layer) of the OSI model.
- TLS uses certificate-based authentication, data encryption, and message integrity verification mechanisms. The use of SSL VPN is mostly in Web-based remote security access.
- TLS uses an eight-step Handshake protocol to establish the identity of a peer, using a combination of public and private keys to initiate encryption.
- TLS uses a Public key infrastructure (PKI) to provide a solution for registering and managing a trustworthy public key.
- Advantages of TLS:
- TLS is the most used encryption technique.
- RFC 7457 (TLS 1.3) is the latest version of TLS; it lists 15 attacks that are mitigated by the new version.
- Disadvantages of TLS:
- The Browser Exploit Against SSL/TLS (BEAST) attack exploits the predictable initialization TLS implementation due to the use of the Cipher Block Chaining (CBC), allowing an attacker to decrypt parts of a packet.
- HeartBleed is a security bug in the OpenSSL cryptography library, which allows an attacker to read the memory of the systems (buffer over-read).
OpenVPN¶
- OpenVPN is an open-source, highly configurable, extremely popular VPN protocol for a variety of ports and encryption types.
- OpenVPN uses the SSL/TLS mechanisms for authentication and encryption and does not suffer from the complexity that characterizes other VPN implementations like market leader IPsec.
- OpenVPN offers two basic modes, which run either as Layer 2 or as Layer 3 VPN.
- OpenVPN tunnels can also transport Ethernet Frames, IPX packets, and Windows Network Browsing packets (NETBIOS), all of which are problems in most other VPN solutions.
- Once OpenVPN has established a tunnel, the central firewall in the company’s central branch can protect any laptop, even if it is not a local machine. Any employee can protected by the central firewall whenever connected.
- OpenVPN can be configured to run as a TCP or UDP service; and as server or client.
- All firewall rules, restrictions, forwarding mechanisms, and concepts like NAT can be used with OpenVPN.
- Advantages of OpenVPN:
- OpenVPN is easy to configure, secure, fast, flexible, and reliable.
- Disadvantages of OpenVPN:
- OpenVPN is not IPsec compatible, and IPsec is the standard VPN solution.
- Many popular network devices, such as Cisco or Bintec routers, use IPsec and can connect to applications of other manufacturers or software IPsec clients.
- Although OpenVPN can be simple to implement, industry knowledge of this protocol, which was introduced in 2001, is somewhat limited.
- OpenVPN is not a multi-thread application, which limits its rate of operating network connections (approximately up to 100 connections). In case more connections are needed, additional processes, different ports or IP addresses need to be deployed.
Which protocol is the most secure?¶
| Protocol | Layer | Notes | * Security Rank 1-4 |
|---|---|---|---|
| L2TP | 2,5 | requires authentication/login which is Layer 5 function. does not provide machine level security. | 3 |
| IPsec | 3 | cannot provide physical and logical tunneling, it relies on L2TP for that. | 2 |
| TLS | 4-7 | 4 | |
| OpenVPN | 3 | not compatible with IPsec/L2TP | 1 |
- WireGuard was recently proposed as a replacement for existing secure communications protocols like IPsec and OpenVPN.
- It has numerous benefits, including its simplicity and ease of configuration, high-performance software, and small codebase.
- All of these make it relatively easy to audit compared to large, complex code bases typically encountered with other protocols
Ping Test 2¶
- Ping is a basic network administration utility (command), similar to traceroute, used to test the reachability of a host on an IP network.
- It works by sending an Internet Control Message Protocol (ICMP) echo request to a specific IP or host address listens to the ICMP echo response and measures the time it takes for the reply to come back to the source.
- It helps in troubleshooting accessibility or performance issues you may be having or simply a quick way to tell if a host is “up” or performing slowly or intermittently poorly.
ping <hostname or IP address> -c <count> -i <interval> -t <ttl>
VPN: Overview and Security Risks 3¶
- VPN stands for Virtual Private Network, which is essentially a private connection over the Internet. It can be implied as an Internet within the Internet.
- PPTP (Point-to-Point Tunneling Protocol):
- PPTP was developed by Microsoft’s Mr. Gurdeep Singh Pall in 1996.
- PPTP was the beginning of VPN technology.
- The security breaches happening from 2002 to 2008 were the key factors responsible for the development of VPN as a technology.
- Reasons people started to sue VPNs:
- VPNs increase online protection, increase online security, and permit to utilize the Web uninhibitedly as they allow a user to go around online limitations and website restrictions.
- VPNs are utilized to secure internet connections, guarantee advanced security, forestall malware and hacking, open geo-hindered content and cover user’s Internet Protocol (IP) and MAC addresses.
- VPNs are generally used as an important tool for remaining sheltered and secure over the Web; and are simple to use and moderately priced.
- Types of VPNs:
- Remote Access VPN:
- It allows a client to link to a secure and private network from any location.
- A link is established between the client and private network through the Internet granting the client access to all resources available on the private network.
- Site-to-Site VPN:
- It is used to connect two or more networks together.
- It is used to connect the networks of two or more organizations or locations of the same organization.
- It is similar to a router-to-router communication VPN.
- One location has a router that acts as a client while the central location works as the main server.
- Remote Access VPN:
Overview of VPN Protocols¶
- PPTP: Point-to-Point Tunneling Protocol.
- Earliest and most used VPN protocol, developed by Microsoft.
- It was designed for dial-up connections.
- It has a lower level of encryption and is not as secure as other VPN protocols.
- The lower level of encryption makes it faster than other VPN protocols.
- It is no longer used.
- IPsec: Internet Protocol Security.
- It is a layer 3 (Network Layer) protocol.
- IPsec provides security to Internet Protocol communication by authenticating the session and ciphering each data packet all along the connection.
- It can be used with other protocols, such as L2TP or SSL, or alone.
- Configuring IPsec can be complex.
- L2TP/IPsec: Layer 2 Tunneling Protocol/Internet Protocol Security.
- It is a combination of PPTP and L2F (Layer 2 Forwarding).
- It generates a tunnel between two connections; both using L2TP and the data packets exchanged between them are enciphered by the IPsec protocol providing a secure connection between the two.
- It is a highly secured protocol with no known susceptibility
- IKEv2: Internet Key Exchange version 2.
- It is a tunneling protocol that was developed by Microsoft and Cisco.
- A Secure key exchange session is carried out by this protocol before communication begins.
- IKEv2 is usually combined with IPsec for encryption and authentication.
- It is excellent for restoring connections once they are lost or dropped.
- It is useful for mobile devices like handsets, tablets and laptops as these devices keep switching between networks from 3G to 4G LTE or from mobile data to Wi-Fi.
- OpenVPN:
- It is an open-source protocol, its underlying code can be accessed by the developers, hence making it a highly configurable protocol.
- It has the best security standards like AES-256 bit key encryption with 2048-bit RSA authentication.
Security issues involved while using VPNs¶
- Logging: VPN providers can log your data, browsing history, and other personal information; and then sell it to third parties.
- Data Leaks: DNS leaks or IP leaks that defy the purpose of using a VPN.
- Weak Privacy Policy: You have no control over the privacy policy of the VPN provider.
- Badly Configured Encryption: VPN providers can use weak encryption standards, and you have no way of knowing.
- Malware Attacks: You are not safe if the VPN provider’s servers are infected with malware.
- Usage of Traditional Protocols like PPTP: some VPN providers still use PPTP, which is not secure.
- IP addresses being used as Exit Nodes: VPN providers can use your IP address as an exit node for other users.
Wireshark 4¶
- Wireshark is a network protocol analyzer that lets you capture and interactively browse the traffic running on a computer network.
- The chapter does not include useful information; however, it includes a quick guide about how to navigate the Wireshark user interface, including capturing, viewing, and filtering captured data packets.
Software-Defined Networking (SDN) 5¶
Network management¶
- It is the process of managing the network infrastructure, including hardware and software, and the services provided by the network. it tries to achieve various tasks:
- Load balancing.
- Security.
- Business relationships.
- Many things can go wrong due to poor network management, such as:
- Persistent Oscillations: routers do not agree on how to route packets to a destination.
- Loops: packets are sent in a loop that evolves the same routers over and over again, and the network is flooded with packets that never reach their destination.
- Partitions: the network is split into two or more parts, and the routers in each part cannot communicate with the routers in the other parts; completely isolated segments.
- Black Holes: packets are sent to a router that does not know how to forward them to the destination, and thus the packets are dropped.
- Traffic Jams: routers are overwhelmed with packets and cannot keep up with the demand.
- Deadlocks: routers are waiting for each other to release resources, and the network is stuck.
- Starvation: some routers are not getting enough resources to do their job.
Software Defined Networking (SDN)¶
- SDN is a new approach to networking that uses software-based controllers or application programming interfaces (APIs) to communicate with the underlying hardware infrastructure and direct traffic on the network.
- Routers and switches are controlled by software, and the network is managed by a central controller instead of the distributed model that was famous before (each router has its own state).
- SDN separates the control plane (which decides how to handle the traffic, and computes routing tables) from the data plane (which forwards traffic according to decisions that the control plane makes).
- SDN consolidates the control plane; so that a single software control program controls multiple data-plane elements.
- In a traditional network, data and control planes are put on the routers.
- In SDN, control is centralized while data is still decentralized.
- SDN started in 2004 as the Routing Control Platform (RCP) for the BGP (Border Gateway Protocol) routing protocol.
- SDN today has 4D planes, after adopting the OpenFlow protocol in 2008:
- Decision Plane: where the control plane makes decisions about how to handle traffic.
- Dissemination Plane: where the control plane sends decisions to the data plane.
- Discovery Plane: where the control plane learns about the network topology and the state of the network.
- Data Plane: where the data is forwarded according to the decisions made by the control plane.
- Advantages of SDN:
- Easier to coordinate and manage the network.
- Easier to evolve, and do Virtual Machine migration in Data Centers.
- easier to debug and troubleshoot.
- Easier to experiment with new protocols and algorithms.
- The Control Plane is programmed using a high-level language, and the Data Plane is programmed using a low-level language but it it accepts OpenFlow commands to control the hardware (switch, router, etc).
- Thus, the Control Plan sends OpenFlow commands to the Data Plane, which can interpret them and execute them.
- SDN can be applied to:
- Data Centers.
- Backbone Networks.
- Enterprise Networks.
- Internet Exchange Points.
- Home Networks.
Traffic Engineering 6¶
Traffic Engineering¶
- It is the process of optimizing the performance of a network by dynamically adjusting the paths of the traffic.
- It is how network operators deal with large amounts of data flowing through their networks. They reconfigure the network in response to changing traffic loads to achieve some operational goals, like:
- Traffic ratios: how much traffic is going from one place to another.
- Relieve congestion: how to avoid traffic jams.
- Balance load: how to distribute traffic evenly across the network.
- The 3 steps of Traffic Engineering:
- Measure: measure the traffic load on the network.
- Model: build a model of the network, and use the model to predict how the network will behave under different conditions.
- Control: use the model to decide how to reconfigure the network to achieve some operational goals, and then reconfigure the network.
- The Model is an objective function that takes the state of the network and the desired goals as input; and produces a set of commands to reconfigure link weights as output.
- Goals that are passed to the model can be:
- Minimize the maximum link utilization: reduce traffic on the most congested link.
- Evenly distribute traffic across the network: balance load.
- Other goals.
- Intra-domain Traffic Engineering:
- In a standard network topology, every link has a weight that represents the cost of using that link.
- The weight can be adjusted to reflect the current state of the network.
- Link weights are inversely proportional to the capacity of the link: the more capacity a link has, the lower its weight.
- Link weights are directly proportional to the propagation delay of the link: the more delay a link has, the higher its weight.
- Inter-domain Traffic Engineering:
- Inter-domain routing is the process of exchanging routing information between different domains, networks, or ASes (Autonomous Systems).
- Inter-domain Traffic Engineering thus involves reconfiguring the BGP policies or configurations that are running on individual edge routers in the network.
- Goals of Inter-domain Traffic Engineering:
- Predictability: predict how traffic will change in response to changes in the network configuration. Downstream neighbors may make changes in response to our changes, which is a problem to us; we should NOT make changes that are globally visible.
- Limit the influence of neighboring domains: we should make consistent route advertisements to make sure that neighboring domains are aware of our state and act accordingly, and consistently (no surprises).
- Minimize the impact of changes: we should make changes that have a minimal impact on the network, and that are reversible.
| Feature | Intra-domain Traffic Engineering | Interd-omain Traffic Engineering |
|---|---|---|
| Scope | Within a single network | Between different networks |
| Protocols | OSPF, RIP, MPLS | BGP |
| Goal | Optimize traffic flow internally | Optimize traffic flow externally |
| Control | Managed by single entity | Negotiated between entities |
- Multi-path Routing:
- Used in Inter-domain and Intra-domain Traffic Engineering.
- Equal Cost Multi-Path (ECMP): Assign the same weight to multiple paths, then the sender can choose any of these paths when forwarding packets (as they have the same weight).
- The source router can still observe the congestion on the downstream links, and decide the percentage of traffic to send on each path on the equal cost paths.
Data Center Networking¶
- Characteristics of Data Center Networking:
- Multi-Tenancy: multiple tenants share the same infrastructure; thus security and resource isolation are important.
- Elastic resources: resources are allocated and deallocated on demand; thus the internal structure of the network should be flexible and expect constant changes.
- Flexible management: the network should be easy to manage, reconfigure, or migrate to a new location within the same or to a different data center.
- Requirements to build Data Center Networks:
- High Bandwidth: to support the large amount of traffic that flows through the network.
- Low Latency: to support the real-time applications that are running on the network.
- High Reliability: to support the mission-critical applications that are running on the network.
- Scalability: to support the large number of servers and clients that are connected to the network.
- Security: to support the multi-tenancy and the elastic resources.
- Load Balancing.
- Support for Virtualization: to support the virtual machines that are running on the network.
- Low Power Consumption: to support the green data center initiatives.
- Provisioning: to support flexible management.
- Layers in Data Center Networking:
- Access Layer:
- Where the servers are connected to the network.
- Usually, has 200x the number of links in the core layer, so that we can avoid the single point of failure.
- Pods are used to group links in access layers, and give them pseudo-MAC addresses; so that the forwarding tables in the layers below are much smaller, as these tables need only to maintain Pods’ MAC addresses, not MAC addresses for every switch in the access layer.
- Aggregation Layer: where the access layer is connected to the core layer.
- Core Layer:
- Where the aggregation layer is connected to the rest of the network.
- Usually, has a layer 2 topology which makes it easier to migrate, but harder to scale.
- Access Layer:
References¶
-
Angelo, R. (2019). Secure protocols and virtual private networks: An evaluation. Issues in Information Systems, 20(3), 37-46. https://iacis.org/iis/2019/3_iis_2019_37-46.pdf ↩
-
How to perform a ping test in Windows, Mac OS, and Linux. (2020, August 9). ChemiCloud. https://chemicloud.com/kb/article/how-to-perform-a-ping-test-in-windows-mac-os-and-linux/ ↩
-
Jadhav, R. R., & Sheth, P. S. (2021). VPN: Overview and security risks. International Journal of Advanced Research in Science, Communication and Technology, 7(1), 305-309. https://ijarsct.co.in/Paper1649.pdf ↩
-
Sharpe, R., Ed Warnicke ., & Lamping, U. (n.d.). Wireshark user’s guide version 4.1.0. Wireshark. https://www.wireshark.org/docs/wsug_html_chunked/ChapterUsing.html. Read Chapter 3: User Interface, to get acquainted with the Wireshark user interface, including capturing, viewing, and filtering captured data packets. ↩
-
Swyx. (2020a, February 23). Networking essentials: Software-defined networking. DEV. https://dev.to/swyx/networking-essentials-software-defined-networking-35n9 ↩
-
Swyx. (2020b, February 23). Networking essentials: Traffic engineering. DEV. https://dev.to/swyx/networking-essentials-traffic-engineering-13c4 ↩