8. OS Security¶
10 Top Linux/Unix Security Vulnerabilities 1¶
- BIND Domain Name System.
- Remote Procedure Call (RPC).
- Apache Web Server.
- General UNIX Authentication Accounts with No Passwords or Weak Passwords
- Clear Text Services
- Sendmail
- Simple Network Management Protocol (SNMP)
- Secure Shell (SSH)
- Misconfiguration of Enterprise Services NIS/NFS
- Open Secure Sockets Layer (SSL)
Critical Security Controls 2¶
- Historically were 20 (called the top 20); in v8, they are 18.
- IG1:
- IG1 is the definition of basic cyber hygiene and represents an emerging minimum standard of information security for all enterprises.
- IG1 is a foundational set of cyber defense Safeguards that every enterprise should apply to guard against the most common attacks.
- IG2 and IG3 build upon previous IGs, with IG1 being the on-ramp to the Controls.
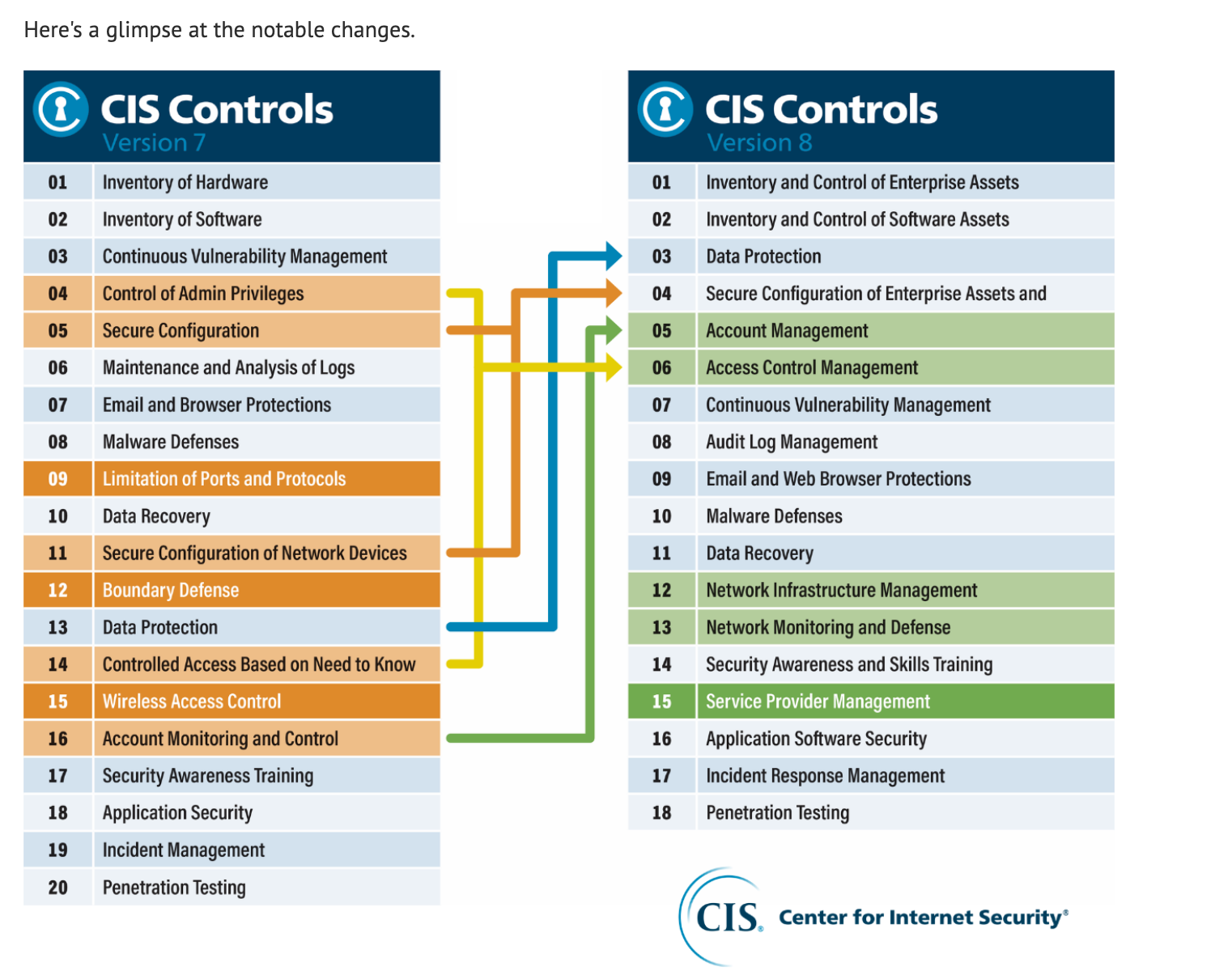
Security Consensus Operational Readiness Evaluation (SCORE) 3¶
- Update the system
apt-get update && apt-get upgrade - Install AppArmor and Bastille.
- Configure and use SELinux.
- Configure and use PAM authentication daemon.
- Shadow File Password Policy.
- Shut down unnecessary services. Some of the services to disable:
- The R commands; for example, rlogin, rsh, rcp, and rexec …etc.
- Fingerd.
- Tftpd.
- Telnet.
- SNMP daemon.
- Remove secure options from terminals.
- Examine the
PATHvariable; remove any ‘.’ or empty strings. - Configure user login sessions to time out automatically.
- LOCK DOWN config-FILES CONTENT
- Sensitive system files need to have the proper permissions set on them to prevent unauthorized changes.
References¶
-
McCormick, J. (November 3, 2003). SANS/FBI releases latest top 10 Linux/UNIX vulnerabilities. http://www.techrepublic.com/article/sans-fbi-releases-latest-top-10-linux-unix-vulnerabilities/ ↩
-
The Critical Security Controls: Twenty Critical Security Controls for Effective Cyber Defense. Retrieved from: http://www.sans.org/critical-security-controls/ ↩
-
SANS Security Checklist: Security Consensus Operational Readiness Evaluation (SCORE). Retrieved from: http://www.sans.org/score/checklists/linuxchecklist.pdf ↩
-
NIST Special Publication 800-53: Security and Privacy Controls for Federal Information Systems and Organizations. Retrieved from: http://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-53r4.pdf ↩
-
The United States Government Configuration Baseline (USGCB)- Red Hat Content. Retrieved from: http://usgcb.nist.gov/usgcb/rhel_content.html ↩