WA5. Buffer Overflow Attacks¶
Statement¶
Conduct online research to explore Buffer Overflow attacks and Vulnerabilities. Write an essay discussing and analyzing Buffer Overflow issues in the present-day scenario. Consider the below points/questions while working on the essay.
- Are buffer overflow attacks a serious threat to applications these days? Why and why not?
- Support your discussion and analysis using a minimum of two examples and research data. Statistical data should not be older than 12 months.
- Use your own words in developing your point of view and making a conclusion.
- Reinforce your arguments with appropriate quotes in the text and research references.
- Must use the APA style for a reference list and quotations in the text.
Solution¶
Introduction¶
Buffer Overflow occurs when a program tries to write to memory more bytes at a time than what the buffer permits; leading to the extra data overwriting the adjacent memory locations. If the program is designed well, it will crash without overwriting any adjacent memory locations; however, if the program does not handle such a case, the entire system becomes vulnerable to exploitation (Cloudflare, 2014, 1).
Buffer overflow attacks target a program that has a buffer overflow vulnerability; the attacker exploits this vulnerability by overwriting the adjacent memory locations with his malicious code and then executes this code to gain access to the system (Cloudflare, 2014, 1).
Low-level languages like C and C++ are more vulnerable to buffer overflow attacks as they do not have built-in protection against such attacks; however, high-level languages like Java, Javascript, and Python do not deal with memory management directly and have built-in protection against buffer overflow attacks (Cloudflare, 2014, 1).
There are different types of buffer overflow attacks depending on the location of memory that is being overwritten; the most common types are stack-based, heap-based, and integer overflow (Cloudflare, 2014, 1).
Here is a diagram showing the number of overflow vulnerabilities that were published in 2013-2023 (CveDetails, 2023, 2):
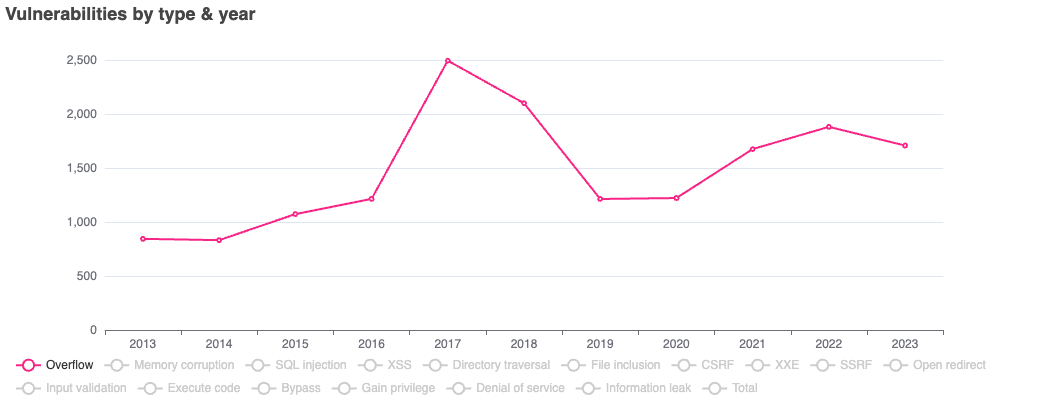
We can see that the number of overflow vulnerabilities is now almost 2 times what it was 10 years ago, with a peak in 2017-2018.
Examples¶
Here are two examples of recent buffer overflow discovered vulnerabilities:
- CVE-2023-4863 (Campbell, 2023, 3):
- It is a buffer overflow vulnerability detected in the widely-used open-source LibWebP library.
- LibWebP is a library for encoding and decoding images in WebP format.
- The vulnerability was discovered on 7 September 2023, by Apple’s security team.
- The library was widely used to the extent caused Apple to issue a security update for all its operating systems (iOS, macOS, watchOS, and tvOS).
- Google also had to update its Chrome browser and most of the major Linux distributions had to issue security updates to fix this vulnerability.
- Luckily, the issue was discovered before any exploitation was reported, otherwise, millions of devices would have been affected.
- CVE-2023-33308 (Mitre, 2023, 4):
- It is a stack-based buffer overflow vulnerability detected in Fortinet FortiOs and FortiProxy.
- It allows a remote unauthenticated attacker to execute arbitrary code or command via crafted packets reaching proxy policies or firewall policies with proxy mode alongside deep or full packet inspection.
- Fortinet itself is a cybersecurity company that provides firewalls, antivirus, intrusion prevention, and endpoint security.
- Thus, if a cybersecurity-as-a-service company like Fortinet is vulnerable, then all of its customers are vulnerable as well.
Conclusion¶
Buffer overflow variabilities are still widely existing in the software industry today, but I don’t think attacks are as serious as they were 10 years ago; as most of the software is now written in high-level languages that have built-in protection against buffer overflow attacks. However, buffer overflow attacks are still a serious threat to low-level languages like C and C++ which most operating, embedded, and IoT systems are written in.
The image below from CveDetails (2023, 2) shows the number of overflow vulnerabilities compared to the total number of vulnerabilities in 2013-2023:
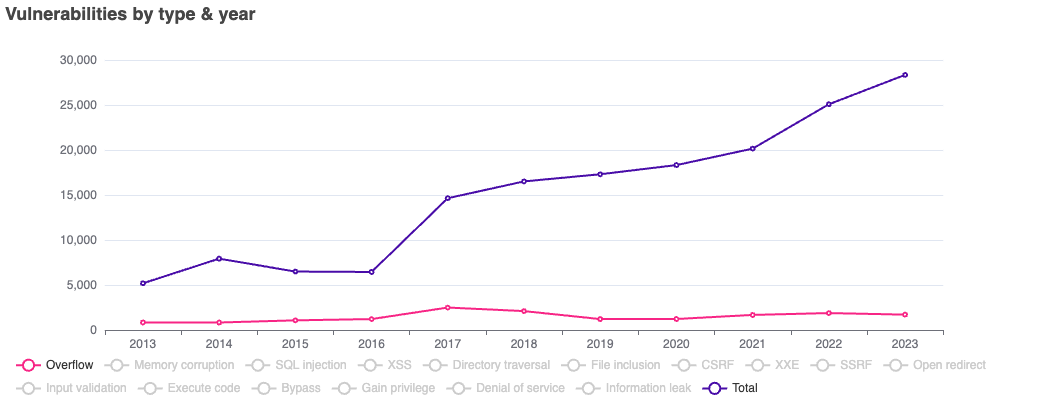
We see that the number of overflow vulnerabilities constitutes a small percentage of total vulnerabilities, and this percentage has been stable over the years.
When it comes to web applications, buffer overflow attacks are not as common as XSS and XXE attacks; as most web applications are written in high-level languages, and web servers are less likely to manage memory directly. However, that does not mean that we -as software professionals- should ignore such a threat.
Instead, we should always aim to use OS runtime protections, keep devices patched, follow the principle of least privilege, use a firewall to block malicious traffic, use a memory-safe programming language, and always validate user input (Cobb, 2021, 5).
References¶
-
Cloudflare. (2014) What is buffer overflow? Cloudflare. https://www.cloudflare.com/learning/security/threats/buffer-overflow/ ↩↩↩↩
-
CveDetails. (2023). Vulnerabilities by type. CVE security vulnerability database. Security vulnerabilities, exploits, references and more. Cvedetails.com. https://www.cvedetails.com/vulnerabilities-by-types.php ↩↩
-
Campbell, S. (2023, October 3). CVE-2023-4863 | Arctic Wolf. Arctic Wolf. https://arcticwolf.com/resources/blog/cve-2023-4863/ ↩
-
Mitre. (2023). CVE - CVE-2023-33308. Mitre.org. https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2023-33308 ↩
-
Cobb, M. (2021). buffer overflow. Security; TechTarget. https://www.techtarget.com/searchsecurity/definition/buffer-overflow ↩